The Difference between Training and Learning:
“An organization’s ability to learn, and translate that learning into action rapidly,
is the ultimate competitive advantage”. ~Jack Welch – Former CEO GE
Is there a difference between training and learning? This is one of the questions that has plagued instructional designers and training organizations for years. Some people are of the mindset that “if we build it (training), they will learn,” while others have only to look at the absence of behavior change to know that someone who participates in training may not always learn and, more importantly, apply, the specified material.
Training departments in organizations around the globe have been fervently trying to develop programs which will allow the adult learner to learn the material at hand, retain it and use it. In order to develop successful training programs that do this, the differences between training and learning must be understood. Training is not learning. We can train someone to hit a baseball in an hour, but it takes years to learn the game.
The first component to understand is training and learning are two distinct, separate functions where learning encompasses training. When a person participates in a training program, learning occurs to some degree. In other words, you cannot be trained without some learning. On the flip side, adult learners can learn without formal training. Autodidacts around the world will attest to that fact. Adult learners can engage in learning through any medium without a traditional curriculum and come out the other side with extreme knowledge. Facilitated training may not provide this type of experience.
One of the key differences between training and learning is individuals generally set out to learn something while training is something that is done to a person. Learning is what an individual does; training is something they receive.
Another key difference between training and learning is learning can occur anywhere at any time; while training is received at a specific place and time. Education is received at a school resulting in a diploma while training generally occurs at a workplace or seminar and a certificate of completion may be received.
In a study performed at the University of Texas, researchers found that individuals retain a mere 10 percent of what they read and 20 percent of what they hear; however, they retain 90 percent of what they do. Adults tend to remember much more by doing than merely by reading or listening.
Another difference between training and learning is individuals embark upon learning something about which they are passionate or see a significant personal benefit, i.e. career advancement. Whereas when someone goes through training, it is usually for a specified outcome. Perhaps they need to attend a training session for continuing education credits or as a job requirement.
ADULT LEARNING
Danish professor Knud Illeris developed a model of adult learning that focused on cognition, emotion and society; all three of which must be present for learning to occur. Illeris assumed that the cognitive element of his model contained knowledge and skills, the emotional element contained feelings and motivation, and society was comprised of communicating with other people (Merriam et al., 2007). According to Illeris, one of five types of “raw material” starts off the learning process. The raw material consists of perception, transmission, experience, imitation and activity.
Conversely, Peter Jarvis’s learning process suggested that all learning begins with experience as well as with the five human senses (Merriam et al., 2007). Unlike McClusky, Illeris and Knowles, Peter Jarvis theorized that the body’s senses played an imminent role in learning; thus becoming the first theorist to emphasize the body/mind connection. While Jarvis recognized the importance of experience which was similar to the theories of the others, he emphasized the importance of body in learning, something that these others neglect.
TRAINING
Training generally occurs in spurts. A person is hired for a new job and must go through training in order to learn the intricacies of systems, machines or other components of the job. Learning, on the other hand, is an ongoing process for many people and they may engage in multiple learning sessions simultaneously. Individuals can learn a new iPhone app, learn a new system at work, learn how to de-clutter their home and learn how to cook a new recipe all in the same day. On the other hand, a training session is generally linear and contains a beginning, middle and ending. Training is often accompanied by an exam or an assessment which will gauge the knowledge of the participant.
It is difficult for training sessions to meet the unique needs of all types of adult learners. For example, if you are to undergo classroom training, you may have a facilitator who will click through slides and “teach” the various content. While this may benefit a visual learner, it leaves a kinesthetic learner and an audio learner in the dark. Often, a variety of mediums are built into the training to ensure the material is retained. For example, a curriculum can be built with classroom training and then on the job training which allows kinesthetic learners access to the hands-on training. Sometimes web-based training will accompany classroom training and, if narrated, will reinforce content for the audio learner.
Another consideration training departments must contend with is the fact material is forgotten by adults over time. The forgetting curve shown in Figure 1 represents how much and how quickly material is forgotten if there is no attempt to refresh the information learned. Organizations that lean toward “one and done” training sessions do not get the return on their training dollar investment.
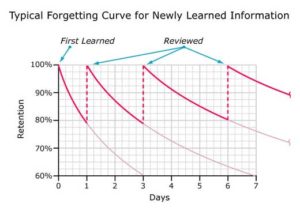
In addition to the “natural” loss of information after a training class, what happens if the adult learner is not interested in learning through training? It is the goal of the training team to offer quality training that engage and motivate the individual learner.
Building a Learning Organization
In an article in 2012, Forbes Magazine reported organizations that implemented formalized learning systems versus training classes outperformed the competition by 3:1. These companies provided coaching, on-demand training and performance support tools which allowed employees to learn and apply content on the job. This type of program is much more successful than simply training people on a curriculum. While training classes may have a place in organizations, high-impact learning practices are proving to be more effective to the organization’s bottom line and achieving mission.

Many organizations are gearing toward the trend of Gamification training to engage employees and ensure training material is retained. As with any new technique to hit the market, there are pitfalls that can occur (Cook, 2013). One major component to watch for when developing Gamification training is this type of training may quickly become the norm. While initially providing competitive games with rewards, badges or other types of achievement icons to motivate employees, people can quickly become bored with the “new toy on the block” and lose interest, ultimately having a detrimental effect on ROI and productivity, the exact opposite of the outcome intended.
One effective way to ensure Gamification training is successful is to make it a special component of an overall continuous learning system, not simply an expensive add-on. Ensure the executive team has buy-in and understands the process of Gamification so employees are held accountable for learning and not merely “playing”.
Implementing adult learning theories into development of Gamification training as well as standard curriculum design will ensure employees are engaged in the training process, retain the content and the adoption of the learning objectives (i.e. new behaviors) are measured and correlated to improved organizational performance and pre-defined metrics.
Gamification and scenario-based simulations and online training provide one answer. These types of programs can be developed to encompass a variety of adult learners. Scenario-based online programs allow kinesthetic learners to navigate through problems or systems allow and have the hands-on processes they need, while accompanying narration and coaching support the auditory learner. Providing motivation through rewards or badges may motivate adult learners to continue through the programs. Competitive individuals may be motivated through leader boards. While no training process may ever reach all types of adult learners and encompass all adult learning theories, these types of programs reach a far wider audience than ever before.
Summary
The significant difference is training is an “event”. Learning is about fully engaging learners in the learning process – preparedness to learn, ensuring relevance of the content to the learner, and providing just-in-time skill development and practices. Learners need to be fully engaged in the learning process because, in today’s complex organizations, it’s not how much you know; it’s how much you use!
This is the business of our business – creating a series of relevant learning content with reinforcement activities that motivate and encourage learners to apply new concepts.
For example, organizations invest millions in their IT infrastructure. The return is directly related to the ability of their people to maximize the use of these technologies for optimum performance. IT personnel don’t need to be trained in required technologies, they need to LEARN, APPLY and SUSTAIN these technologies.
At ABL, we draw the crucial distinction between training and learning in all our offerings, as evidenced in our IT learning platform for Cisco, Microsoft and Project Management. In every course, we utilize all of the following:
- Live, on-line, HD quality classes
- Front line interaction with top quality instructors
- Communities of Practice (COP)
- 24×7 access to the Live recorded classes for both learning preparation and reinforcement
- Real gear, Live online hands-on labs
- 24×7 Mentorship Program with Instructors
We are turning our client’s employees into “Active Learners”. By incorporating these various components, we enable the student to select what they need, when they need it and in what form they want it. We strengthen learning by providing pathways from knowledge to application and interactions that form lasting learning and effective recognition and recall.
Please feel free to contact us to discuss how we can support ensuring your ROI on training investments.
References
Bersin, J. (2012) 5 Keys to Building a learning Organization. Retrieved from: http://www.forbes.com/sites/joshbersin/2012/01/18/5-keys-to-building-a-learning-organization/
Chapman, A. (2006). Kolb learning styles. Retrieved from http://www.businessballs.com/kolblearningstyles.htm
Cook, W. (2013) Training Today: 5 Gamification Pitfalls. Training Magazine. Retrieved from: http://www.trainingmag.com/content/training-today-5-gamification-pitfalls
Hansman, Catherine A. (2001) Context-based adult learning. New Directions for Adult and Continuing Education, no. 89, pp. 43-46.
Kilgore, Deborah W. (2001) Critical and postmodern perspectives on adult learning. New Directions for Adult and Continuing Education, no. 89, pp 53-55.
Klumpke, A. E. (n.d.). The Seneca Falls convention. Retrieved from http://www.npg.si.edu/col/seneca/senfalls1.htm
Merriam, Sharan B. (2001) Andragogy and self-directed learning: Pillars of adult learning theory. New Directions for Adult and Continuing Education, no. 89, p. 5.
Merriam, Sharan B., Rosemary S. Caffarella, and Lisa M. Baumgartner, (2007) Selections, Learning in adulthood: A comprehensive guide, 3rd Edition, Jossey-Bass, pp. 27-51, 83-103, 189-215, 226-239
Mezirow, J. (1997). Transformative learning: theory to practice. Retrieved from http://www.ecolas.eu/content/images/Mezirow Transformative Learning.pdf
Neill, J. (2005, January 26). Retrieved from http://wilderdom.com/experiential/JohnDeweyPhilosophyEducation.html
Nobelprize.org. (2011). Retrieved from http://www.nobelprize.org/nobel_prizes/peace/laureates/1931/addams-bio.html
40th anniversary of the adult education act timeline. (2007, October 16). Retrieved from http://www2.ed.gov/about/offices/list/ovae/pi/AdultEd/anniv40/doe.html




