by Craig Cocciola | Nov 27, 2017 | Cyber Security, Cybersecurity Jobs
ABL Cyber Lab brings experience to Cyber Certification Courses
LAB Overview
The ABL Cyber Lab is for both beginner and intermediate level cyber skills building. The ABL Cyber Lab training programs provide students with an interactive environment to learn the use of powerful hacking tools to scan, attack, test and build the required real-world skills to discover website and application vulnerabilities. The Lab is a secure way to learn and practice on internal, non-public web servers. The Lab training is not conducted in controlled simulations. Users are provided lessons on ABL Lab servers which allow them to progressively learn in a safe environment. Through the use of tools in Kali Linux, they scan and discover flaws and weaknesses known to be used by attackers to compromise systems. By gaining the hands-on experience of offensive tactics, cyber security professionals are able to prepare and determine the most effective strategy for defense.
In addition to many others, Lab students learn Pen Testing and how to perform:
- Wireless Attacks
- using aircrack-ng, fern Wi-Fi and Kismet
- Web Application Analysis
- Burpsuite, OWASP-Zap, SQLmap, WPScan
- Sniffing and Spoofing
- Metasploit, ettercap, wireshark, netsniff-n
- Information Gathering
- netdiscover, NMap, recon-ng
- Cyber Exploitation Tools
- Social Engineering ToolKit, Metasploit, Armitage, BeEF
Cyber Lab Skills-Based Training
All ABL Cyber Lab students have access to over 200 Kali linux pre-installed tools. Upon completion of all Beginner and Intermediate Lab lessons, all students receive a Certificate of Completion. The Lab experience provides hands on experience which is critical to supplement industry standard certification preparation training. This combination ensures the individual has the knowledge and practical skills to add value to his/her team and help identify poorly designed code and vulnerable system configuration critical to protecting any organization.
Closing the gap in cybersecurity skills requires a national agenda to develop critical technical skills, cultivate a larger and more diverse workforce, and reform education and training programs to include more hands-on learning.
TOUR the ABL Cyber Lab: Take a 2 minute video tour of the ABL Cyber Lab, at the ABL Cyber Academy....
NOTE: ABL uses a fully vetted and tested video hosting services. These are Safe links.
- Wireless Attacks
- Web Application Analysis
- Sniffing and Spoofing
- Information Gathering
- Cyber Exploitation Tools
Many others…

Contact ABL Cyber Lab:
Craig Cocciola, FSO Director IT
480-525-7195 direct
craig@advancedbusinesslearning.com
by Craig Cocciola | Sep 7, 2017 | Cyber Security, Cybersecurity School, Ethical Hacker, News
Cybersecurity Jobs are Knocking – certifications will open the door
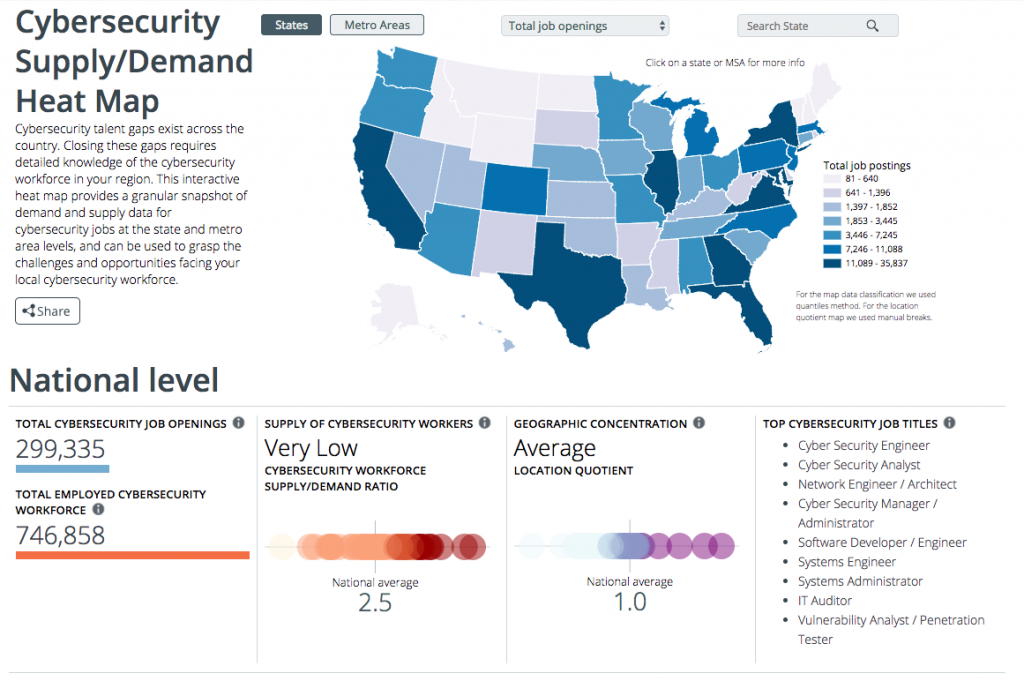
FACT: the number of job postings requiring IT or cybersecurity certifications, are far greater than the supply of those holding these credentials. College degree is NOT required to work and grow in IT or Cybersecurity careers.
visit: CyberSeek.org or DOWNLOAD 3192-CyberSeekFlyer-FINAL-online INFO SHEET
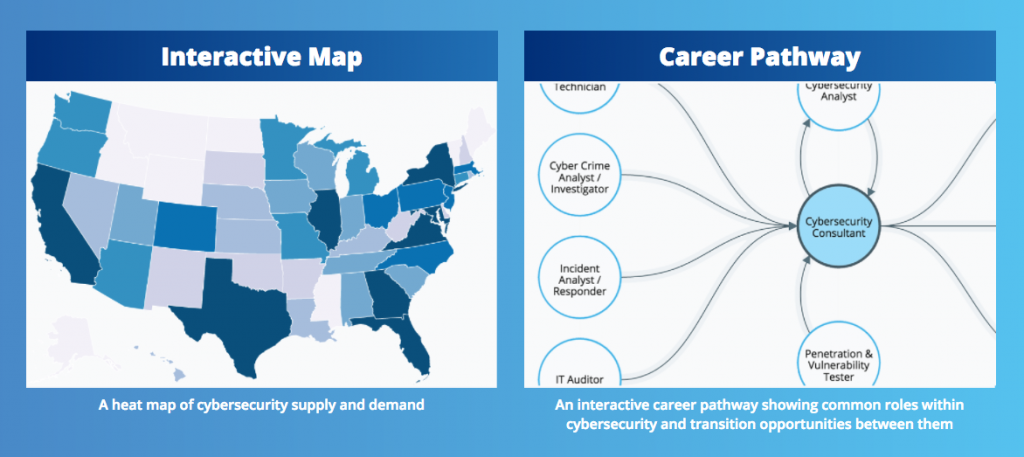
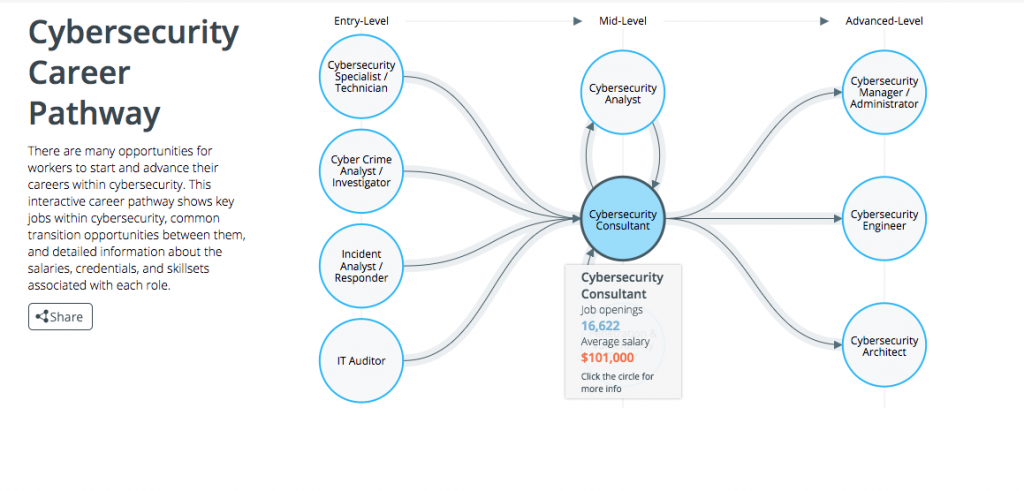
Available Cyber Career Analysis Tools
> Cybersecurity Supply And Demand Heat Map
> Cybersecurity Career Pathway
by Craig Cocciola | Sep 7, 2017 | CISSP Certification Arizona, Cyber Security, News
CISSP Courses November 2017
- Blended Live Mentor and Online Course is structured to meet student timelines
- ABL Cyber LAB included for both onsite and remote access – real world skills building ethical hacking our vulnerable websites and apps
- DoD grade Instructors
- Location 10 minutes West of ASU
- Government Pricing available for Educational, Financial and Large Commercial Organizations
Price incl. Tuition and Books: $3596 – exam fee and CISSP Mentor support included
November Courses: Get Course Info from Link below
CISSP – Certification Prep Course
by Craig Cocciola | Sep 1, 2016 | Cybersecurity Certifications, Cybersecurity School, Knowledge Center, News
Phoenix Cybersecurity Training School Offers New Learning Experience
As stout advocates against “learning decay” (the loss of retention of learned material over time) Advanced Business Learning (ABL) has developed a unique process that not only fights learning decay but helps students retain and relearn over time.
E-Learning (or web-based curriculum) done right involves working with the organization’s subject matter experts to distill the key skill-based learning elements and creating actionable scenarios the participant can immediately apply on their job. Couple this with targeted reinforcements to ensure just in time, just as needed rapid learning transference to the job.
To help stem this learning decay over a period of time and ensure the transfer of learning to actual job performance, a Continuous Learning System (CLS) should be incorporated into any learning solution. This is an inventory of tools and content designed to enhance learning sustainment by delivering reinforcement training in live, virtual, or blended environments.
This “menu” approach is intended to be “mixed and matched” and configured based on specific requirements, situations, and readiness levels. Examples of CLS elements include:
- Meetings in a box: Interactive discussions about best practices. Sustainability guides provide specific actions participants will take before, during, and after courses to promote the transfer and sustainability of learning
- E-toolkits/Mobile Learning: Electronic cache of performance application, reinforcement, and support tools for easy access to updated course materials. Posted content may include, but is not limited to, Best Practice analyses, lessons learned, job aids, media assets, sample communications, templates, social media sharing tools, blogs, technical manuals
One example of Mobile learning or M-learning is to create targeted learning at the fingertips of users. This can be accomplished via Quick Response Code (QR Codes) posted on key equipment that links to a Learning Management System providing immediate access to instruction manuals, videos, job aids, micro-learning elements and scenarios on how to use the equipment to help the individual be effective in working with that specific equipment.
Users with a camera phone/smart tablet/laptop equipped with the correct reader application can scan the image of the QR code to display text, contact information, connect to a wireless network, or open a web page in the browser. This act of linking from physical world objects is termed hard linking or object hyperlinking. QR codes can be used to log into websites: a QR Code is shown on the login page on a computer screen, and when a registered user scans it with a verified smartphone, they will automatically be logged in. Authentication is performed by the smartphone which contacts the internal server.
ABL’s unique approach to E-learning methods of training and processing information with continual technology-based reinforcement has proven to be a tactical advantage for employers looking to train their workforce. Employees are out-of-pocket for a short amount of time and return to work with a new base of expertise and the tools to retain the curriculum they just absorbed without a steep drop off from learning decay.
by Craig Cocciola | Aug 26, 2016 | Ethical Hacker, Insider Threats, Knowledge Center, News
What is an Insider Threat?
Is the threat to your organization someone you know and trust? An Insider Threat may be intentional or just bad work habits, poor training and personal behaviors. Both intended and unwitting threats are significant problems. Ignoring questionable behaviors can only increase the potential damage the insider can have on your organization, the national security and/or employee safety. While each insider threat may have different motivations, the indicators are generally consistent.
Be Alert! Be Aware! Report suspicious activity to your local security official. See something, say something. Nine times out of ten, after an attack on data or people, someone realizes they knew something that could have stopped or reduced the damages, or even deaths.
Insider Threat Examples of possible Reportable Behaviors – Information Data Collection
- – Keeping classified materials in an unauthorized location
- – at home, car, backpack, bag, personal server
- – Attempting unauthorized access to private or classified data information
- – Obtaining access to sensitive information beyond the requirements of a person’s job
- – A request from a worker or team member to provide access or documents without a current need or out of their project access
- – Questionable data or file downloads
- – Gathering information which has no relevancy to assigned work
- – Unauthorized use of removable media and moving files without permission
- – Using an unclassified medium to move classified materials
- – Unsecured faxing, thumb drives, external hard disks
- – Discussing classified topics and materials on non-secure phones, using non-secure emails or texts
- – Use of cellphone in or out of workplace on home phone or personal email or texting
- – Removing the classification markings from documents
- – Changing the classification or observing deleting classified markings
- – Unnecessary or excess copying of classified materials
- – Nervous behaviors around unusual activities
- – Moving data to external drives or any out of pattern heavy usage of copy machines
- – Expressing loyalty to another country or for a radical cause
- – Displays desire to help, assist or fight for a foreign faction
- – Concealing reportable foreign travel or contact
- – Sudden reversal of financial situation or a sudden repayment of large debts or loans
- – Mysterious purchase of new car, expensive jewelry or large investments
- – Being disgruntled to the point of discussing or writing about the desire to retaliate
- – “I’ll get them for this” or “she’s going to pay for that”
- – Repeated or unrequired work outside of normal duty hours
- – Bringing an unapproved BYOD or work device into a unauthorized or controlled area
What’s in it for me to take the risk of reporting something?
Insiders have a negative impact on your industry, our nation’s security and safety and well-being of the citizens. Not reporting can seriously affect your career or even cause you big legal problems. The effect of not reporting, often will result in:
Not reporting can seriously affect your career or even cause you big legal problems.
The effect of not reporting, often will result in:
- – Loss or compromise of private information, of classified or controlled and sensitive information
- – Military weapons can be reproduced, destroyed, or rendered ineffective
- – The country’s loss of technological competitiveness or superiority
- – Financial loss, company brand and image damage causing layoffs or slowing economic growth
- – Public utilities and infrastructure damage and physical harm, and loss of life
Take the Insider Threat seriously. It’s worth doing the right thing over the cost of keeping quiet.
To find out what steps you can take in creating Insider Threat awareness, and the requisite change management for your organization, call Susan Morris or Tom Jenkins today.
480-222-7507 office or 480-227-5134 direct




