by Craig Cocciola | Sep 7, 2017 | Cyber Security, Cybersecurity School, Ethical Hacker, News
Cybersecurity Jobs are Knocking – certifications will open the door
FACT: the number of job postings requiring IT or cybersecurity certifications, are far greater than the supply of those holding these credentials. College degree is NOT required to work and grow in IT or Cybersecurity careers.
visit: CyberSeek.org or DOWNLOAD 3192-CyberSeekFlyer-FINAL-online INFO SHEET
Available Cyber Career Analysis Tools
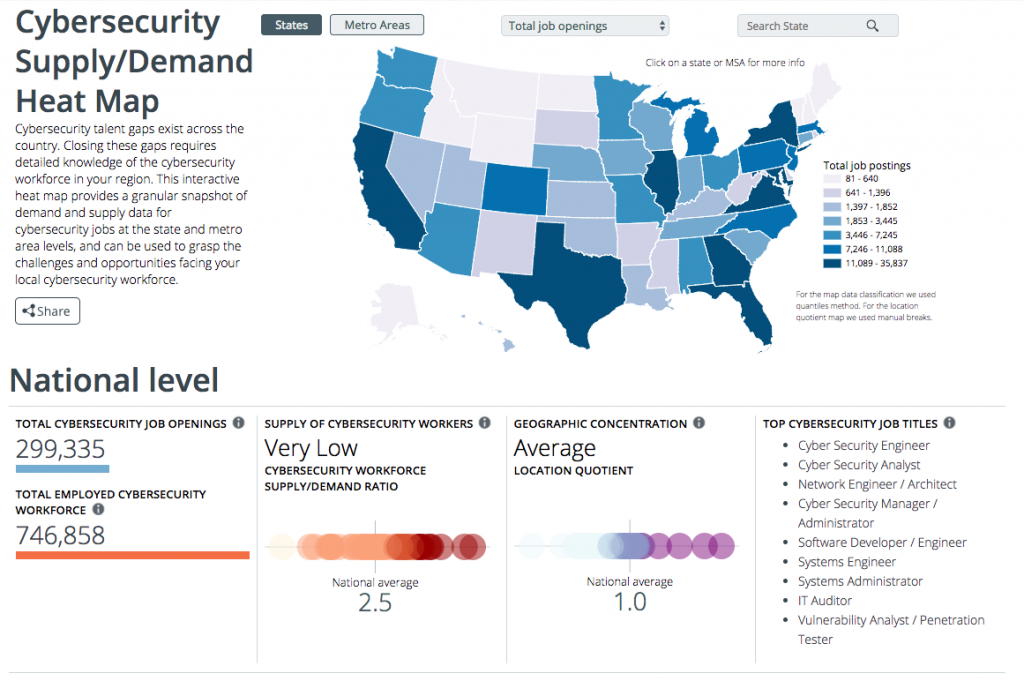
> Cybersecurity Supply And Demand Heat Map
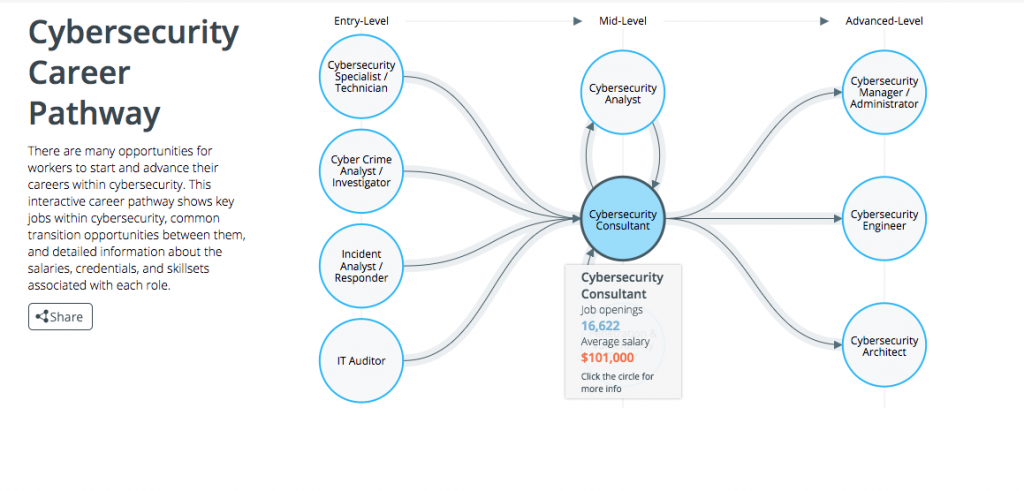
> Cybersecurity Career Pathway
by Jason Jantzen | Sep 6, 2016 | Cyber Security, Cybersecurity School, Ethical Hacker, News
Recent cyberattacks on corporations like Target, Banner Health and most recently public voter data have influenced corporations to take a much more offensive approach to their internal cybersecurity practices. As companies like Uber are shifting away from a traditional brick and mortar organization to a more cloud based platform, the need to protect consumer information has increased exponentially. Modern day ways of doing business now have much less to do with cash as they do a smart phone transaction.
To avoid any setbacks or loss of consumer trust, companies have been forced to rethink their approach to protecting consumer data from a “wait and see” to having skilled and educated employees in place who now take preemptive measures to test strategies and best practices before a breach occurs.
A recent study by CompTIA, a leading resource for the IT industry, has shown that companies now consider security one of the primary responsibilities of their IT team. Larger organizations may have a subset of individuals whose sole responsibility is protecting consumer data while other smaller companies rely on well trained individuals with Network+ or CISSP certifications leading the helm.
Long gone are the days where a simple firewall was sufficient security. Corporations must now assess vulnerability of data not only within but also vet the security capabilities of vendors with whom they work. An example of this would be third party credit card processors or cloud based CRM platforms like Salesforce who are trusted daily with detailed consumer information.
Regardless of the security measures a company takes, CompTIA has also found that the most common source of breached data is caused by human error—specifically untrained employees. Internal efforts to educate employees on cybersecurity best practices often fall short, creating a need for classroom based learning in a short amount of time.
Advanced Business Learning, a licensed State of Arizona postsecondary vocational school and a CompTIA Authorized Training Provider, offers a wide variety of courses which properly prepare workforces to meet today’s challenges in security management. Companies who wish to improve the knowledge base of their workforce can enroll employees in entry-level to advanced CompTIA courses which establish best practices in troubleshooting, networking and security across a variety of devices in a 5-day bootcamp. For those IT departments on the offensive, they may consider the investment in having their top IT professionals becoming ISC2 certified and ultimately becoming a Certified Information Systems Security Professional (CISSP).
by Craig Cocciola | Aug 26, 2016 | Ethical Hacker, Insider Threats, Knowledge Center, News
What is an Insider Threat?
Is the threat to your organization someone you know and trust? An Insider Threat may be intentional or just bad work habits, poor training and personal behaviors. Both intended and unwitting threats are significant problems. Ignoring questionable behaviors can only increase the potential damage the insider can have on your organization, the national security and/or employee safety. While each insider threat may have different motivations, the indicators are generally consistent.
Be Alert! Be Aware! Report suspicious activity to your local security official. See something, say something. Nine times out of ten, after an attack on data or people, someone realizes they knew something that could have stopped or reduced the damages, or even deaths.
Insider Threat Examples of possible Reportable Behaviors – Information Data Collection
- – Keeping classified materials in an unauthorized location
- – at home, car, backpack, bag, personal server
- – Attempting unauthorized access to private or classified data information
- – Obtaining access to sensitive information beyond the requirements of a person’s job
- – A request from a worker or team member to provide access or documents without a current need or out of their project access
- – Questionable data or file downloads
- – Gathering information which has no relevancy to assigned work
- – Unauthorized use of removable media and moving files without permission
- – Using an unclassified medium to move classified materials
- – Unsecured faxing, thumb drives, external hard disks
- – Discussing classified topics and materials on non-secure phones, using non-secure emails or texts
- – Use of cellphone in or out of workplace on home phone or personal email or texting
- – Removing the classification markings from documents
- – Changing the classification or observing deleting classified markings
- – Unnecessary or excess copying of classified materials
- – Nervous behaviors around unusual activities
- – Moving data to external drives or any out of pattern heavy usage of copy machines
- – Expressing loyalty to another country or for a radical cause
- – Displays desire to help, assist or fight for a foreign faction
- – Concealing reportable foreign travel or contact
- – Sudden reversal of financial situation or a sudden repayment of large debts or loans
- – Mysterious purchase of new car, expensive jewelry or large investments
- – Being disgruntled to the point of discussing or writing about the desire to retaliate
- – “I’ll get them for this” or “she’s going to pay for that”
- – Repeated or unrequired work outside of normal duty hours
- – Bringing an unapproved BYOD or work device into a unauthorized or controlled area
What’s in it for me to take the risk of reporting something?
Insiders have a negative impact on your industry, our nation’s security and safety and well-being of the citizens. Not reporting can seriously affect your career or even cause you big legal problems. The effect of not reporting, often will result in:
Not reporting can seriously affect your career or even cause you big legal problems.
The effect of not reporting, often will result in:
- – Loss or compromise of private information, of classified or controlled and sensitive information
- – Military weapons can be reproduced, destroyed, or rendered ineffective
- – The country’s loss of technological competitiveness or superiority
- – Financial loss, company brand and image damage causing layoffs or slowing economic growth
- – Public utilities and infrastructure damage and physical harm, and loss of life
Take the Insider Threat seriously. It’s worth doing the right thing over the cost of keeping quiet.
To find out what steps you can take in creating Insider Threat awareness, and the requisite change management for your organization, call Susan Morris or Tom Jenkins today.
480-222-7507 office or 480-227-5134 direct
by Craig Cocciola | Aug 23, 2016 | Cyber Security, Cybersecurity Certifications, Cybersecurity Jobs, Ethical Hacker, News
Best CyberSecurity 5 Day Classes to Earn Certifications
As companies find themselves becoming more and more vulnerable to data breaches, employers in Arizona are increasingly looking within to hire or promote employees who have obtained cybersecurity certifications to ward off future potential attacks. Corporations like Target, who have recently fell victim to a data breach not only pay millions in costly fines but also lose consumer trust and future goodwill.
CompTIA Security +
Job seekers within the growing technology trade in Phoenix who wish to obtain a commercial cybersecurity job or land a coveted IT security position within the defense industry must receive certification as a prerequisite from a state certified school. Depending on the position desired, candidates can start their career with a basic CompTIA certification in network security while top-tier candidates seek the coveted Certified Information Security Manager (CISM). CompTIA certification gives candidates a good overview of best practices in troubleshooting, networking and security across a broad array of devices. Although the CompTIA certification is seen as a stepping stone for more advanced levels of certification, it’s important to note its relevancy as it is required by all employees of the U.S. Department of Defense.
Certified Ethical Hacker
An industry in Arizona that is rapidly growing in popularity is “Ethical Hacking” or “White Hat Hacking.” Ethical hackers must be properly trained and certified because of the high level of trust that is commanded by these positions. Ethical hackers are a unique breed whose main job is to think like a malicious cybercriminal while using that information to protect its employer. In order to properly train individuals to perform this job function, candidates are encouraged to obtain a Certified Ethical Hacker (CEH) certification. Certified Ethical Hackers are often referred to as “penetration testers” and are actually encouraged to attempt to penetrate a company’s network without physically stealing any data. Those who are able to successfully balance this mental game are also well rewarded as salaries start within the six figure range.
Certified Information Systems Security Professional
One of the most popular certifications prospective job seekers can obtain is that of a Certified Information Systems Security Professional (CISSP). Generally obtained by experienced IT professionals, consultants and auditor and risk management professionals, this certification serves as a base requirement for employees securing a company’s network. While the certification doesn’t focus on a single vendor, it does cover a wide array of topics from physical security to cryptography. Those who fully capitalize on the CISSP certification can make in excess of $150,000 per year.
Certified Information Security Manager
The Certified Information Security Manager (CISM) certification is a top-tier certification for those who have at least five years of experience within the network security industry. The CISM classes are very rigorous and will demand every bit of your five years’ background in IT. Those completing this advanced certification will learn about the following four area of cybersecurity:
- > Information security program development and management
- > Information security management
- > Information security incident management
- > Information risk management and compliance
Completion of this certification has the potential to roll out an invitation to the C-suite as CISM’s often obtain Chief Information Security Officer positions and command in excess of $200,000 annually.



